
If you are a Netflix subscriber, you may have received an email notice recently telling you to change your password as soon as possible.
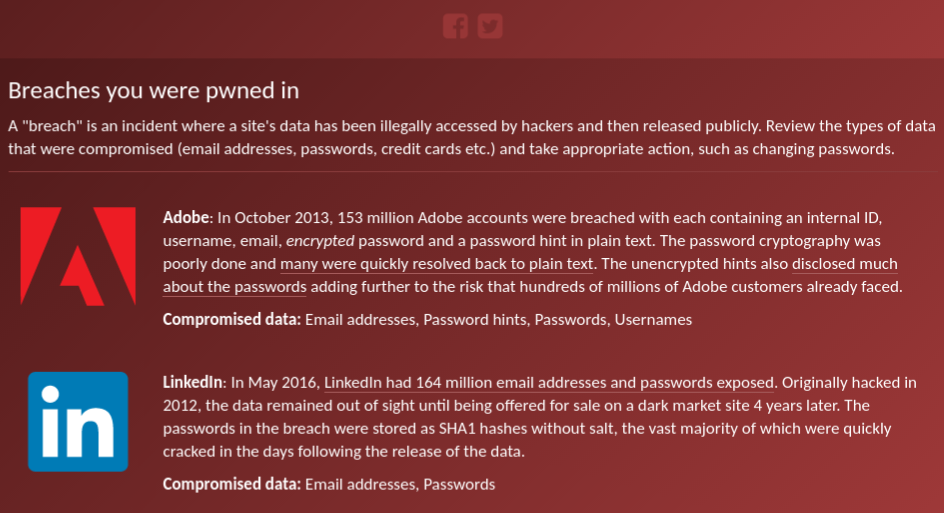
In fact, if you’ve been paying attention to the news recently you will have noticed there has been a cluster of recently exposed megabreaches involving more than 642 million passwords belonging to users of LinkedIn, Twitter, and even long-forgotten Myspace.
There seems to be a new one every week. Here are a few examples:
- Twitter locks some accounts after 32 million passwords (June, 2016)
- Hackers Breach Over 1,100 Websites, Steal 45 Million Passwords (June, 2016)
- ISP suffers massive password leak online (June, 2016)
- Amazon Implements Password Reset after Credentials Leaked Online (April, 2016)
Password Hacks: Lose Control of Your Entire Life
In some cases, a password breach is an annoyance that can be fixed by changing your password. Other times, getting your password hack means losing control of your entire life. Many of us with Yahoo, Hotmail and Gmail accounts have years of our life stored online.
Online accounts also typically contain sensitive credit card and banking information. Even worse, many online services depend on email accounts for help logging in. For example, if you’ve ever forgotten a password for Pinterest or Facebook, you typically need to use an email address that is officially associated with the social media account for help getting back in. If your email account is compromised, you can totally lose control of your entire life.
How Mark Zuckerberg’s Password Got Hacked
No one is immune from having their password stolen. For example, Facebook founder Mark Zuckerberg’s Twitter and Pinterest accounts were recently hacked.

How did the hackers get access to Mark Zuckerberg’s Twitter and Pinterest accounts? It turns out a password breach at another social networking site earlier was to blame. This past May, LinkedIn, a social networking site for professionals, announced that a staggering 117 million passwords were stolen. All of the passwords were uploaded to the Internet where anyone could see them.
Zuckerberg’s LinkedIn password was one of them.
Most People Use the Same Simple Password Across Multiple Sites
Zuckerberg’s password for LinkedIn was dadada. Hackers put two-and-two together and discovered Zuckerberg reused his LinkedIn password on Twitter and Pinterest, and were briefly able to hack into his accounts (and this was before millions of Twitter passwords were hacked just this past June).
Mark Zuckerberg’s experience highlights several common themes about password theft in 2016:
- people tend to use simple passwords
- people tend to reuse their passwords
- security breaches happen all the time
And, perhaps most importantly, anyone, including the head of one of the world’s most sophisticated internet companies, can have their online accounts hacked.
Password ‘Worst’ Practices: Things We All Do, But Really, Really Should Not
There are some pretty common mistakes when making passwords that everyone knows (even if they often ignore):
- Using the same password everywhere
- Never changing your password
- Using information that’s easy to obtain, such as your birthday, as part of your password
However, there are some other mistakes people often make when creating a password, such as:
Letters Only
More secure passwords consist of combinations of numbers, special characters or punctuation marks as well as a mix of upper and lower case letters throughout the password.
Short in Length
The shorter a password, the more opportunities for observing, guessing, and cracking it. A strong password is at least 8 characters long. Some organizations now enforce a minimum length and variety of characters to help strength the company passwords.
Too Old
You’ve used the same password for years. Usually it will take a hacker a very long time to crack a long, complex password. If you change your password every 90 days or as required by your computer network, then the chances of your password being cracked are even more diminished.
Here are the 10 most popular passwords in the world… is yours one of them? These “top ten” passwords have of course been identified in part by countless data breaches:
- password
- 123456
- 12345678
- 1234
- qwerty
- 12345
- dragon
- pussy
- baseball
- football
How to Protect Yourself: Two-Factor Authentication
The problem is, even the best password in the world can be hacked. As many people have discovered at LinkedIn and Twitter in June, some of the largest internet companies in the world can be compromised, releasing your password details to anyone and everyone.
And, what happens if the email account you use for online banking gets hacked? Your banking details are laid bare, and there’s not much you can do about it. Strong passwords are just not enough.
This is where two-factor authentication comes in. What is two-factor authentication? The easiest way to understand it is to think about how you log in, for example, to your email account today. You go to the login page, type in your username and password, and log in. It’s just one step.
With two-factor authentication, it takes two steps to log in, usually with the help of a mobile phone, or another email account.
If you have used Twitter or even Facebook, you may have encountered two-factor authentication before. You attempt to login to Twitter, and Twitter than asks you to produce a code texted to your mobile phone. Google and Microsoft actually have a special code generator app that does away with the need for receiving texts.
This can be annoying because if you don’t have your mobile phone — perhaps it’s out of charge — you can’t receive the text or code, and you can’t login to your account.
Or, sometimes when attempting to login to an online account (Outlook.com, Microsoft’s email service does this), you’ll be emailed a special code to an email account associated with the web service. Once again this can be frustrating if for some reason you can’t login to the associated account.
On the other hand, potential hackers are presented with the same problem: if they do not have access to your mobile phone or your backup email but they try to hack into your account, they can’t receive the extra security code they need to login.
So this added protection of a “second factor” of authentication — proof someone needs to login to your email account — generally keeps you safe.
Generally. But even two-factor authentication can be hacked.
How Two-Factor Authentication Can Be Hacked, And What You Can Do About It
Two-factor authentication can be hacked: there’s an “easy” way, and there’s a harder way. With the easy way, a hacker may simply hack into and take over the email account that receives the security code you need to log in. It’s just an email account, and it can be hacked.
Sending a security code via text message should be more secure, since it’s less likely that a hacker someplace has access to your mobile phone. However, hackers who have figured out your account can actually “spoof” you, and can trick you into sending them the security code from your phone. The hackers may text you or call you up, pretending to be from your bank or even from Gmail. You send them the code, and they can get access to your account.
Disaster!
So, two-factor authentication can still be beaten. However, it’s still the best way to keep your passwords safe, so, to beat the hackers: never, ever share a security code with anyone online. Always keep them to yourself.
Keep Your Computer Safe, Too
You should also be aware that, unless you take precautions, hackers can steal passwords from your computer, too. The best defense this threat is to install and deploy an effective and updated antivirus and anti-spyware solution that features a strong anti-phishing mechanism.
For example, CompuClever Antivirus PLUS features an ironclad information safety mechanism called Data Protection. Data Protection prevents sensitive data leaks when you are online. Based on the rules you create, Data Protection scans the web, e-mail, and instant messaging traffic sent by your computer. It looks for specific character strings, for example, your credit card number. If there is a match, the respective web page, e-mail, or instant message is blocked.
And that keeps you safe online.
Charles Edwards frequently writes about Windows and PCs. If you have some ideas of topics you would like us to cover, email us at:newsletter@compuclever.com.
